Default to Isolation in K-12: Lessons in Cybersecurity Leadership
“We certainly use the least privilege access control. So far so good. Also network segmentation.” That is how Mark Parsons summarizes the heartbeat of Inter-Lakes School District’s network posture. Chapter 5 of the K-12 Cybersecurity Framework calls this move “default to isolation,” a shift from trusting the internal network to allowing only what you explicitly approve. In a world where students test boundaries and malware tries every lateral hop, isolation keeps a mistake in one corner from crashing the whole district.
If our last blog, Essential Hygiene,helped raise your PROTECT scores, isolation is how you keep those gains. The Cybersecurity Rubric flags isolation weaknesses in the IDENTIFY and PROTECT functions: missing segmentation, overly broad permissions, and weak monitoring of what crosses between zones. This post translates the framework guidance and the rubric signals into a rollout plan that works with instructional reality.
What Isolation Looks Like in K-12 Leadership
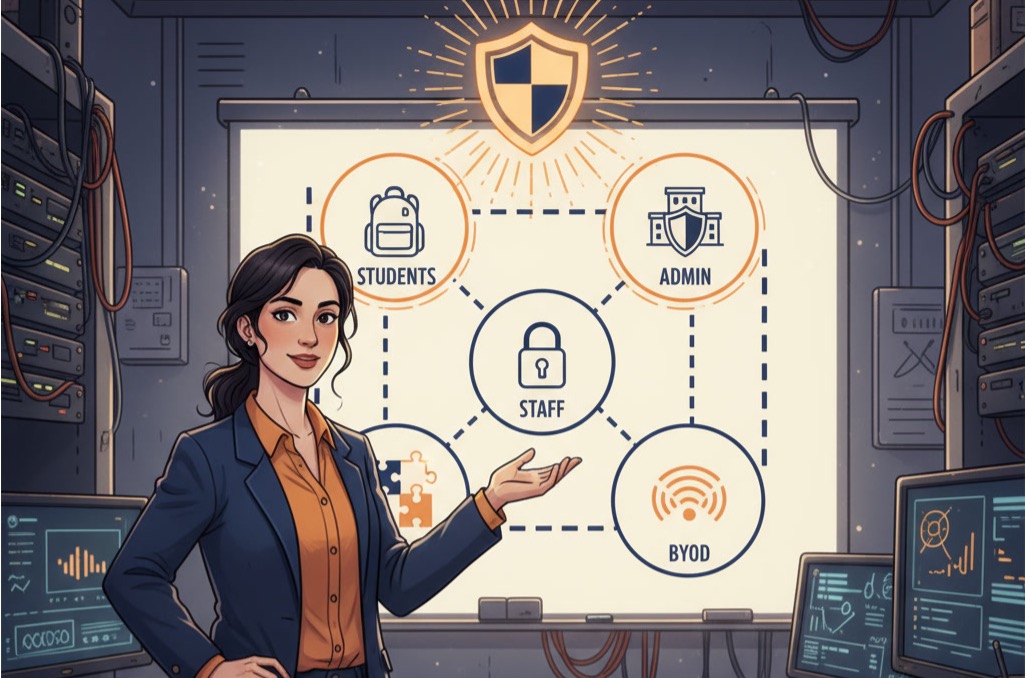
Caroline Lightfoot at Dickinson ISD puts it plainly: “Our primary default-deny practice is through our endpoint firewalls. These are set up to block all traffic by default and only allow what we explicitly permit.” In her district, leadership teams separated student, staff, administration, and BYOD networks so a compromise in one zone does not move elsewhere. They paired those segments with endpoint firewalls on teacher laptops that block outbound connections unless the district approves them. They locked down SIS administrator accounts behind MFA and least privilege access so even insiders cannot roam freely. Each decision required principals, curriculum leaders, and technology leaders to sit together and weigh instructional flexibility against risk, and leadership alignment kept the rollout smooth.
Dana Castine uses the image everyone remembers. “I was taught a long time ago to make sure the viper is in a different cage from the bunny.” She frames isolation as a leadership responsibility: keep high value assets away from curious students, then add controls around the cages so the doors only open when you intend them to. Her leadership lens keeps stakeholders grounded in the why even when the how is complex.
The Rubric Warning Signs Leadership Should Watch
District leadership teams usually notice the same three signals before committing to isolation. Network segmentation feels flat because wireless and wired networks share the same broadcast domain and student devices can see staff devices. Administrative rights stay broad because teachers install software at will and vendors keep SIS admin accounts long after they finish a project. Monitoring remains thin because logs do not show which VLAN traffic crossed and unauthorized devices linger quietly on guest Wi-Fi. Chapter 5 of the framework highlights those failure modes and pairs them with implementation steps. When superintendents and CIOs treat the rubric as a leadership dashboard, IDENTIFY.AM-5 (asset isolation) and PROTECT.PR.AC-3 (least privilege) scores start climbing.
Isolation Pillars That Depend on Leadership
Segmentation architecture has to map to real life. Start with four core segments: students, staff, administration, and BYOD. If VLANs already exist, leadership needs to confirm they enforce separation, map critical systems to each zone, and document which systems must talk to each other. Access control lists and firewall policies should permit only necessary flows while keeping state assessment connections intact. Without leadership backing, that mapping work stalls.
Least privilege only sticks when leaders champion it. Removing local admin rights from classroom devices and moving to role-based access in SIS platforms means communicating why change is happening and how support will respond. Mark Parsons’ team showed that once least privilege is in place, segmentation rules become easier to enforce because fewer users demand exceptions. Their board and superintendent backed the cultural shift, and teachers understood that leadership was protecting instruction time, not taking tools away.
Endpoint firewalls and a default deny stance act as the safety net. Dickinson ISD blocks outbound traffic by default and approves specific destinations. That approach stopped malware more than once. Caroline Lightfoot admits it also slowed innovation occasionally, so they built an exception process with quick turnaround. Leadership made it easy to request and approve exceptions while keeping the default set to “no,” showing staff that security and creativity can coexist when leaders respond quickly.
Edge visibility and validation keep isolation honest. Dan Klimke from NetAlly described walking a building with CyberScope to find rogue hotspots that bypassed filters. Isolation is only as good as a district’s ability to spot workarounds. Leadership-sponsored edge visibility programs show every device on each segment, alert on unknown devices, and map traffic patterns. When leaders insist that every rogue device alert is logged and resolved, culture changes and isolation policies hold.
Implementation Playbook for Cybersecurity Leadership
Successful isolation projects begin with a leadership-backed discovery. Technology directors inventory and classify zones using network diagrams and switch configurations to confirm that every port and SSID lands in the right segment. Superintendents and cabinet leaders communicate why the work matters for student safety and instructional continuity. Once the inventory is clear, leadership authorizes a pilot of least privilege. The pilot might start with a single campus or business unit, removing local admin rights, scoping SIS roles, and documenting the support requests that surface. Leaders listen, adjust timelines, and celebrate the first teams that embrace the change.
With least privilege underway, leadership approves the rollout of endpoint firewall policies. Security staff apply the default deny template to a controlled set of devices, gather feedback, and tune the exception workflow. Communication from principals and technology leaders keeps the community calm while the team learns. Monitoring becomes the next leadership priority. Districts deploy edge visibility tools, VLAN-aware logging, and alerts for unauthorized connections. Cabinet-level sponsorship ensures the monitoring team has time and authority to act on what they see. Finally, leadership guides the phased expansion. Once the pilot holds, they scale zone by zone, communicating which services are moving and when. Leaders stay visible during each phase so staff know the district is steering the change, not reacting to it.
Measuring Progress for Leadership Accountability
Metrics keep leadership honest. Districts tie isolation measures to rubric controls and review them in executive sessions: the percentage of critical systems isolated from student networks, the number of devices running with least privilege, the average time required to approve firewall exceptions, and the pace at which unauthorized device detections are resolved. Incident reviews feed the same dashboards. Districts that complete these steps report a seventy to ninety percent reduction in malware spread, faster containment when a student tries something creative, and more reliable Wi-Fi performance for instruction. Leadership teams use those outcomes to brief boards and community members on the value of the investment.
Next Steps for District Leaders
Cyber governance committees should prioritize isolation phases together. Bring the current network map, rubric scores in PROTECT and IDENTIFY, and the Chapter 5 checklist from the K-12 Cybersecurity Framework. Decide which segment to harden first and schedule the work for the next break in instruction. Encourage every building leader to nominate a staff liaison so isolation work aligns with teaching priorities. The upcoming blog in this series will cover vendor management, keeping internal and third-party access aligned under a single leadership strategy.
Ready to move? Review Chapter 5 in the framework, share this post with your infrastructure team, and pick one segment to isolate before the next school year. Leadership commitment today keeps classrooms learning when the next attack hits tomorrow.