Cyber Leadership Essentials: Cyber Hygiene that Works in K-12
Caroline Lightfoot still remembers the first time Dickinson ISD tried to push a security control that touched every classroom. “MFA has been one of the easiest to implement,” she told us. “Our dedicated networking team took a very hands-on approach. They made it a priority to train each campus staff during faculty meetings.” Every teacher, para, and front office professional got one-on-one support. The rollout landed smoothly because people were seen, not just directed. That human layer is the difference between a checklist control and cyber hygiene that sticks in a school district.
Essential cyber hygiene is not glamorous, but it is the bedrock of the K-12 Cybersecurity Framework. Chapter 4 spells it out clearly: build the basics well and every other security investment becomes easier to manage. For districts working through the Cybersecurity Rubric, hygiene is the fastest path to raising PROTECT scores in controls like Identity Management, Access Control, Platform Security, and Data Security. The math is simple. Reduce easy attack paths, shorten recovery time, and make the most of the people you already have.
What the Rubric Is Telling You
Rubric scores in the PROTECT function expose the daily friction between security best practices and instructional reality. We consistently see the same gaps:
- Administrative accounts without MFA. CIS IG1 calls MFA a basic control. Attackers see it as an open invitation when it is missing.
- Endpoint drift. Chromebook and Windows devices fall behind on critical updates, especially when state testing regimes freeze browser versions for weeks.
- Backups without validation. Many districts do nightly exports, but few test restores or isolate copies from ransomware.
- Password and timeout fatigue. Unions push back when controls slow teachers who are juggling attendance, grading, and student support.
None of these findings mean teams are ignoring security. They mean the work of school is relentless, and every control has to honor that reality. The framework calls this out directly: cyber hygiene in K-12 succeeds when the rollout plan respects the classroom.
Voices from the Field
Dana Castine at Florida Union Free puts it bluntly. “ALL OF THEM have been challenging. Change is incredibly difficult for everyone and when it involves technology, it becomes even more difficult.” Her team still pushed through MFA by front-loading support. “We provided a great deal of notification, support, training and immediate onsite assistance on the implementation day. We also initiated MFA with a very small group of staff over the course of the school year. We celebrated successes which made staff less apprehensive.”
Caroline Lightfoot echoes the same theme. “This organized, district-wide push, with direct human support, was key to its successful and relatively smooth adoption.” Teachers saw helpdesk staff at their campus. Questions were answered in real time. The measure stuck.
These stories remind us that hygiene controls fail when they are delivered as compliance ultimatums. They succeed when they are implemented as professional learning and operational support.
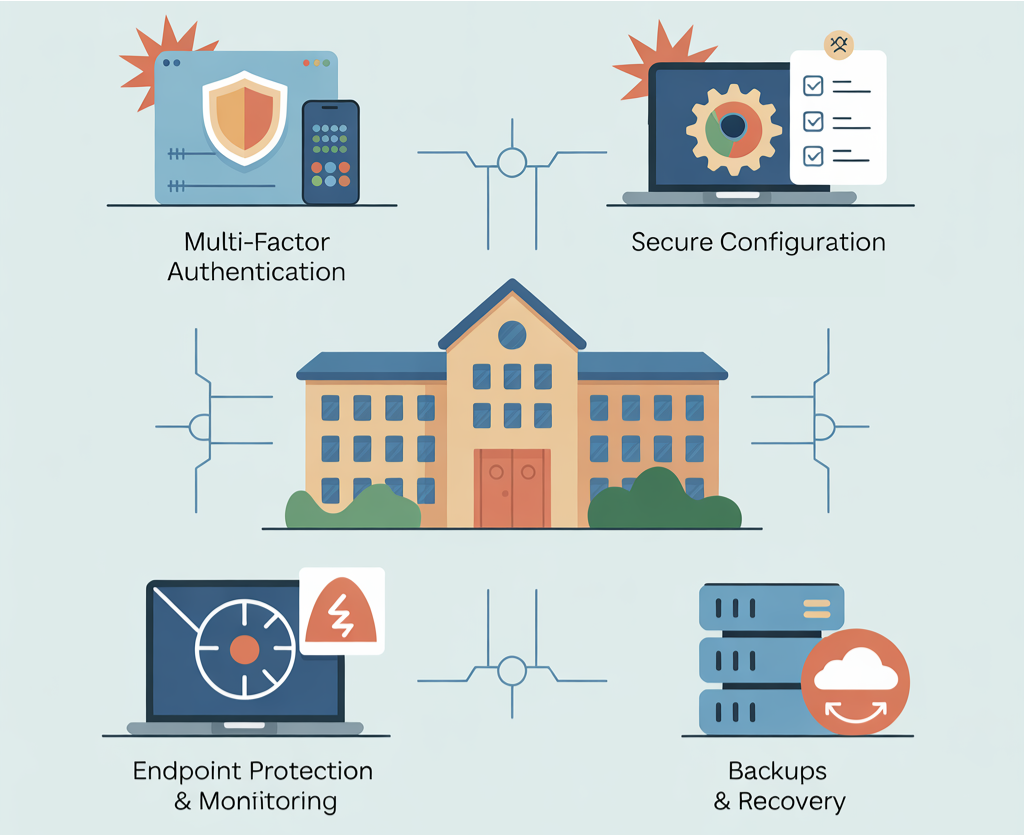
Four Hygiene Pillars You Can Tackle Now
Multi-Factor Authentication for Privileged Accounts
Start with administrative SIS accounts, finance systems, and district-wide collaboration platforms. Give staff two or three enrollment paths, including an authenticator app option for those who cannot receive SMS. Provide live support during faculty meetings and office hours during the rollout week. Track adoption by campus and celebrate the first 100 percent sites to keep energy up.
Secure Configuration without Derailing Instruction
Configuration is where theory meets the STAAR testing calendar. Dickinson ISD discovered that auto updates on Chromebooks break the state testing client when the Chromebook OS moves faster than STAAR. The practical lesson: build configuration baselines that include testing exceptions, document them, and schedule a short window after testing to catch up. Use a shared tracker so curriculum, testing, and IT see the same risk tradeoffs.
Endpoint Protection and Monitoring with Automation
Small teams cannot babysit dashboards all day. Dickinson ISD uses CrowdStrike Falcon Complete because it quarantines suspicious files, isolates devices, and rolls back changes automatically. “This automation has been a game-changer for maintaining compliance with controls like Malware Defenses and Continuous Vulnerability Management,” Lightfoot said. Choose a platform that integrates with your existing identity stack and sends real alerts to the people who can act quickly.
Backups and Recoveries That Actually Work
Daily SIS and cloud service backups only matter when they restore cleanly. Schedule a monthly tabletop exercise where someone restores a subset of data to a sandbox environment. Keep at least one copy of critical backups offline or in immutable storage. Measure backup success by time to recovery, not just copy completion.
Implementation Playbook
- Prioritize by risk and effort. Map MFA, segmentation, backups, and endpoint protection against your most critical systems. Start where the student impact is lowest and the risk reduction is highest.
- Stage rollouts around the academic calendar. Use teacher workdays, summer refresh cycles, and the week after testing windows close.
- Prepare supports. Offer live help, short how-to videos, and quick reference guides. Pair tech staff with instructional technology coaches when possible.
- Collect feedback. Survey staff after each rollout and adjust policies that create unnecessary friction. Share wins to build momentum.
Measuring Progress
Tie your metrics to the rubric so leadership sees the payoff:
- Administrator MFA adoption rate (target 100 percent).
- Percentage of devices on current patch level (target 95 percent inside two weeks of release or testing window close).
- Verified backup restores per month (target at least one success per critical system).
- Staff satisfaction for hygiene rollouts (target average rating above 4 on a 5-point scale).
Combine these metrics with incident data. Districts with disciplined hygiene see 60 to 80 percent fewer successful phishing and malware events and recover 70 to 90 percent faster when something does slip through.
Next Steps
Use the Essential Cyber Hygiene Checklist to score your current state. Bring the results to your cyber governance committee and pick one pillar to complete each quarter. If you want the deeper playbook behind each pillar, open Chapter 4 of the K-12 Cybersecurity Framework linked at K12Leaders.com/cybersecurity and walk through the implementation guidance with your team. Once the foundation is in place, you will be ready for the next post in this series: Default to Isolation, where we will unlock segmentation strategies that keep your network resilient without shutting down learning.
Ready to get started? Review your Cybersecurity Rubric scores in the PROTECT domain, then use this hygiene plan to raise your baseline before summer turnover.
Resources:
The K-12 Cybersecurity Framework